Opening statement
Encryption has emerged as a critical necessity in the realm of software development, particularly in light of the risks tied to handling sensitive information. This imperative extends not only to safeguarding data within our internal systems but also to securing data transmitted over networks.
A noticeable trend has arisen wherein an increasing number of projects demand AES encryption for enhancing the security of data during transit. Consequently, we’ve chosen to disseminate this knowledge, aiming to provide assistance not only to the MuleSoft community at Apisero but also to those beyond in their efforts to implement this specific use case.
Application scenario
Transform the JSON payload information into an AES-encrypted Base64 encoded string for sending it to the downstream systems. The downstream system will then decipher the payload using the identical AES key and IV value, thereby augmenting the overall security of the procedure.
Terminology Guide
AES (Advanced Encryption Standard) is a widely adopted standard employed for safeguarding and securing sensitive data. It finds application in the encryption of electronic data during its transmission over networks. AES operates on a confidential key, employed by one system for encryption and other systems for decryption.
An initialization vector (IV) serves as an additional layer of security, ensuring that multiple encryptions of the same value using the same secret key will yield distinct encrypted outputs, bolstering the protection of the data.
Execution Specifics
At the outset, the MuleSoft Crypto module was employed, utilizing the JCE Encrypt operation. However, during the implementation phase, complications arose when downstream applications struggled to decipher the payload with the same AES key.
The MuleSoft crypto module lacked the provision to configure a static IV value, as it relied on a random IV value.
To resolve this issue, Java logic was crafted to encrypt the JSON payload using the AES key and IV value.
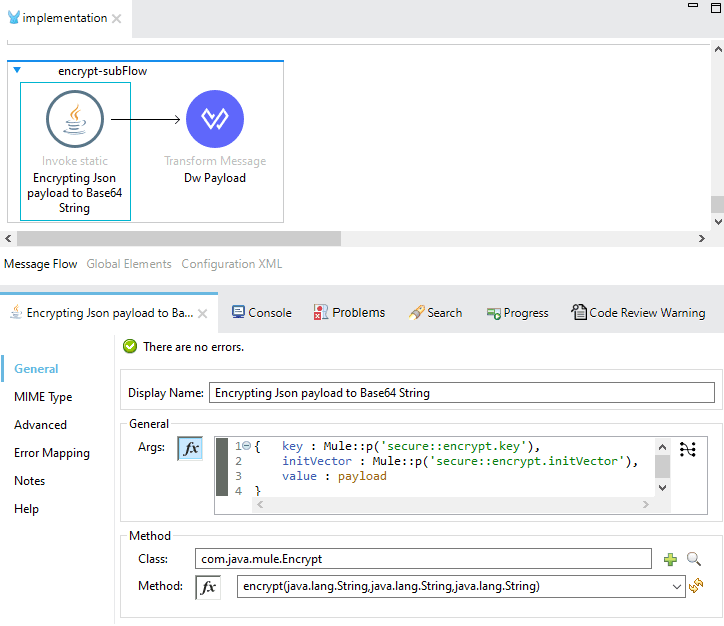
Below, you will find the Java code for encryption based on the AES Key and AES IV. You should pass the payload, AES Key, and AES IV as values, keys, and initVector parameters to the encrypt() method.
package com.java.mule;
import javax.crypto.Cipher;
import javax.crypto.spec.IvParameterSpec;
import javax.crypto.spec.SecretKeySpec;
import java.util.Base64;
public class Encrypt
{
public static String encrypt(String value,final String key,final String initVector)
{
try {
IvParameterSpec iv = new IvParameterSpec(initVector.getBytes("UTF-8"));
SecretKeySpec skeySpec = new SecretKeySpec(key.getBytes("UTF-8"), "AES");
Cipher cipher = Cipher.getInstance("AES/CBC/PKCS5PADDING");
cipher.init(Cipher.ENCRYPT_MODE, skeySpec, iv);
byte[] encrypted = cipher.doFinal(value.getBytes());
return Base64.getEncoder().encodeToString(encrypted);
} catch (Exception ex) {
ex.printStackTrace();
}
return null;
}
}
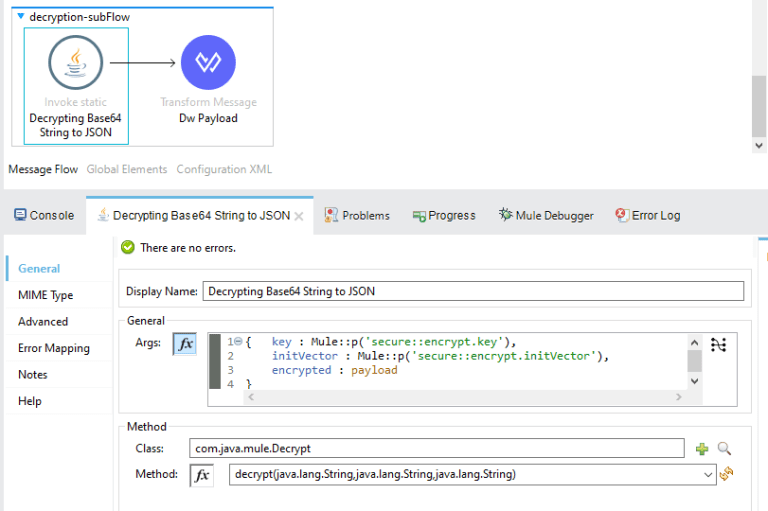
Here is the code for deciphering the encrypted string by utilizing the AES key and AES IV to verify the encryption.
package com.java.mule;
import javax.crypto.Cipher;
import javax.crypto.spec.IvParameterSpec;
import javax.crypto.spec.SecretKeySpec;
import java.util.Base64;
public class Decrypt
{
public static String decrypt(String encrypted, String key,String initVector) {
try {
IvParameterSpec iv = new IvParameterSpec(initVector.getBytes("UTF-8"));
SecretKeySpec skeySpec = new SecretKeySpec(key.getBytes("UTF-8"), "AES");
Cipher cipher = Cipher.getInstance("AES/CBC/PKCS5PADDING");
cipher.init(Cipher.DECRYPT_MODE, skeySpec, iv);
byte[] original = cipher.doFinal(Base64.getDecoder().decode(encrypted));
return new String(original);
} catch (Exception ex) {
ex.printStackTrace();
}
return null;
}
}
Once the Java code is prepared, invoke the logic from within the Mule implementation using the MuleSoft Java module’s Invoke Static operation, as illustrated below.
Here is the code logic for decrypting the JSON payload.
Example
Here is a sample demonstrating the encryption of a JSON payload using an AES key and initialization vector.
{
"name": "Max Mule",
"email": "max.mule@test.com"
}
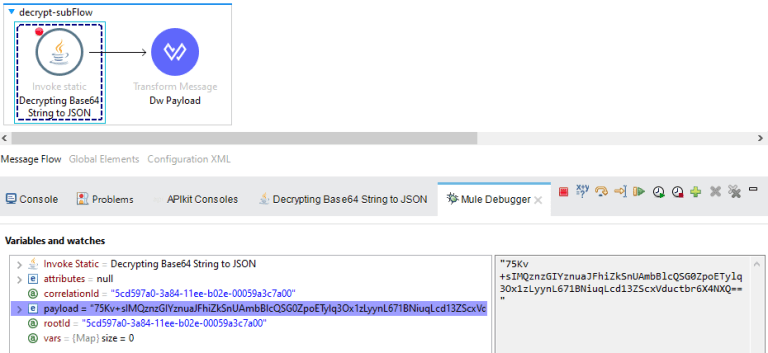
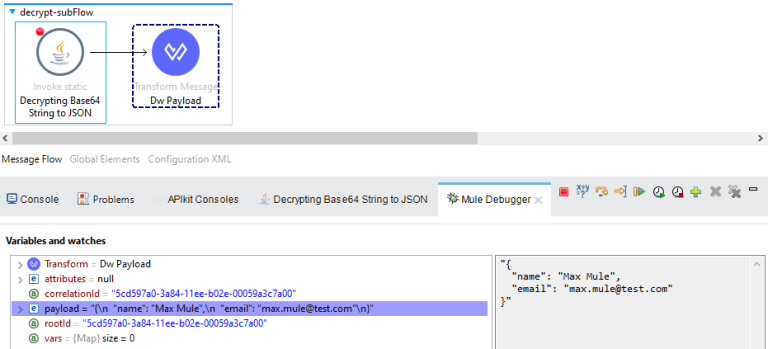
The screenshots below depict the payload during transit and its corresponding encrypted representation.

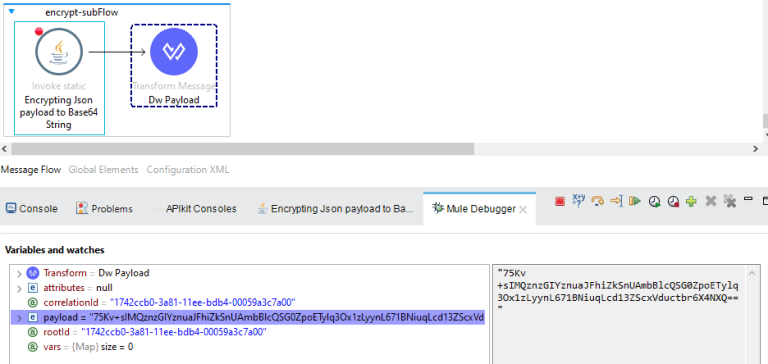
In the screenshot below, we can observe the decryption process of the previously secured value using the identical AES key and initialization vector. As demonstrated, the value is successfully decrypted to the same JSON payload employed earlier.